Tampilkan postingan dengan label Mikrotik. Tampilkan semua postingan
Tampilkan postingan dengan label Mikrotik. Tampilkan semua postingan
Minggu, 27 April 2014
SETUP MIKROTIK OS (UNTUK BILLING HOTSPOT) DIBELAKANG PFSENSE (PROXY LUSCA)
# RouterOS 5.25
#
#
/interface ethernet
set 0 arp=enabled auto-negotiation=yes cable-settings=default \
disable-running-check=yes disabled=no full-duplex=yes l2mtu=16383 \
mac-address= mtu=1500 name=Public speed=100Mbps
set 1 arp=enabled auto-negotiation=yes cable-settings=default \
disable-running-check=yes disabled=no full-duplex=yes mac-address=\
mtu=1500 name=Local speed=100Mbps
set 2 arp=enabled auto-negotiation=yes cable-settings=default \
disable-running-check=yes disabled=no full-duplex=yes mac-address=\
mtu=1500 name=Antena speed=100Mbps
/interface wireless security-profiles
set [ find default=yes ] authentication-types="" eap-methods=passthrough \
group-ciphers=aes-ccm group-key-update=5m interim-update=0s \
management-protection=disabled management-protection-key="" mode=none \
name=default radius-eap-accounting=no radius-mac-accounting=no \
radius-mac-authentication=no radius-mac-caching=disabled \
radius-mac-format=XX:XX:XX:XX:XX:XX radius-mac-mode=as-username \
static-algo-0=none static-algo-1=none static-algo-2=none static-algo-3=\
none static-key-0="" static-key-1="" static-key-2="" static-key-3="" \
static-sta-private-algo=none static-sta-private-key="" \
static-transmit-key=key-0 supplicant-identity=MikroTik tls-certificate=\
none tls-mode=no-certificates unicast-ciphers=aes-ccm wpa-pre-shared-key=\
"" wpa2-pre-shared-key=""
/ip hotspot profile
set [ find default=yes ] dns-name="" hotspot-address=0.0.0.0 html-directory=\
hotspot http-cookie-lifetime=3d http-proxy=0.0.0.0:0 login-by=\
cookie,http-chap name=default rate-limit="" smtp-server=0.0.0.0 \
split-user-domain=no use-radius=no
add dns-name="" hotspot-address=192.168.12.1 html-directory=hotspot \
http-proxy=0.0.0.0:0 login-by=http-chap name=hsprof1 nas-port-type=\
wireless-802.11 radius-accounting=yes radius-default-domain="" \
radius-interim-update=received radius-location-id="" \
radius-location-name="" radius-mac-format=XX:XX:XX:XX:XX:XX rate-limit="" \
smtp-server=0.0.0.0 split-user-domain=no use-radius=yes
/ip hotspot user profile
set [ find default=yes ] idle-timeout=none keepalive-timeout=2m name=default \
shared-users=1 status-autorefresh=1m transparent-proxy=no
add advertise=no idle-timeout=1m keepalive-timeout=2m name=siswa \
open-status-page=always shared-users=10 status-autorefresh=1m \
transparent-proxy=yes
/ip ipsec proposal
set [ find default=yes ] auth-algorithms=sha1 disabled=no enc-algorithms=3des \
lifetime=30m name=default pfs-group=modp1024
/ip pool
add name=hs-pool-3 ranges=192.168.12.2-192.168.12.250
/ip dhcp-server
add address-pool=hs-pool-3 authoritative=after-2sec-delay bootp-support=\
static disabled=no interface=Antena lease-time=1h name=dhcp1
/ip hotspot
add address-pool=hs-pool-3 addresses-per-mac=2 disabled=no idle-timeout=5m \
interface=Antena keepalive-timeout=none name=hotspot1 profile=hsprof1
/port
set 0 baud-rate=9600 data-bits=8 flow-control=none name=serial0 parity=none \
stop-bits=1
set 1 baud-rate=9600 data-bits=8 flow-control=none name=serial1 parity=none \
stop-bits=1
/ppp profile
set 0 change-tcp-mss=yes name=default only-one=default \
remote-ipv6-prefix-pool=none use-compression=default use-encryption=\
default use-ipv6=yes use-mpls=default use-vj-compression=default
set 1 change-tcp-mss=yes name=default-encryption only-one=default \
remote-ipv6-prefix-pool=none use-compression=default use-encryption=yes \
use-ipv6=yes use-mpls=default use-vj-compression=default
/queue type
set 0 kind=pfifo name=default pfifo-limit=50
set 1 kind=pfifo name=ethernet-default pfifo-limit=50
set 2 kind=sfq name=wireless-default sfq-allot=1514 sfq-perturb=5
set 3 kind=red name=synchronous-default red-avg-packet=1000 red-burst=20 \
red-limit=60 red-max-threshold=50 red-min-threshold=10
set 4 kind=sfq name=hotspot-default sfq-allot=1514 sfq-perturb=5
set 5 kind=none name=only-hardware-queue
set 6 kind=mq-pfifo mq-pfifo-limit=50 name=multi-queue-ethernet-default
set 7 kind=pfifo name=default-small pfifo-limit=10
/routing bgp instance
set default as=65530 client-to-client-reflection=yes disabled=no \
ignore-as-path-len=no name=default out-filter="" redistribute-connected=\
no redistribute-ospf=no redistribute-other-bgp=no redistribute-rip=no \
redistribute-static=no router-id=0.0.0.0 routing-table=""
/routing ospf instance
set [ find default=yes ] disabled=no distribute-default=never in-filter=\
ospf-in metric-bgp=auto metric-connected=20 metric-default=1 \
metric-other-ospf=auto metric-rip=20 metric-static=20 name=default \
out-filter=ospf-out redistribute-bgp=no redistribute-connected=no \
redistribute-other-ospf=no redistribute-rip=no redistribute-static=no \
router-id=0.0.0.0
/routing ospf area
set [ find default=yes ] area-id=0.0.0.0 disabled=no instance=default name=\
backbone type=default
/routing ospf-v3 instance
set [ find default=yes ] disabled=no distribute-default=never metric-bgp=auto \
metric-connected=20 metric-default=1 metric-other-ospf=auto metric-rip=20 \
metric-static=20 name=default redistribute-bgp=no redistribute-connected=\
no redistribute-other-ospf=no redistribute-rip=no redistribute-static=no \
router-id=0.0.0.0
/routing ospf-v3 area
set [ find default=yes ] area-id=0.0.0.0 disabled=no instance=default name=\
backbone type=default
/snmp community
set [ find default=yes ] addresses=0.0.0.0/0 authentication-password="" \
authentication-protocol=MD5 encryption-password="" encryption-protocol=\
DES name=public read-access=yes security=none write-access=no
/system logging action
set 0 memory-lines=100 memory-stop-on-full=no name=memory target=memory
set 1 disk-file-count=2 disk-file-name=log disk-lines-per-file=100 \
disk-stop-on-full=no name=disk target=disk
set 2 name=echo remember=yes target=echo
set 3 bsd-syslog=no name=remote remote=:: remote-port=514 src-address=0.0.0.0 \
syslog-facility=daemon syslog-severity=auto target=remote
/tool user-manager customer
add backup-allowed=yes disabled=no login=admin password=78121 \
paypal-accept-pending=no paypal-allowed=no paypal-secure-response=no \
permissions=owner signup-allowed=no time-zone=-00:00
/user group
set read name=read policy="local,telnet,ssh,reboot,read,test,winbox,password,w\
eb,sniff,sensitive,api,!ftp,!write,!policy" skin=default
set write name=write policy="local,telnet,ssh,reboot,read,write,test,winbox,pa\
ssword,web,sniff,sensitive,api,!ftp,!policy" skin=default
set full name=full policy="local,telnet,ssh,ftp,reboot,read,write,policy,test,\
winbox,password,web,sniff,sensitive,api" skin=default
/interface bridge settings
set use-ip-firewall=no use-ip-firewall-for-pppoe=no use-ip-firewall-for-vlan=\
no
/interface l2tp-server server
set authentication=pap,chap,mschap1,mschap2 default-profile=\
default-encryption enabled=no keepalive-timeout=30 max-mru=1460 max-mtu=\
1460 mrru=disabled
/interface ovpn-server server
set auth=sha1,md5 certificate=none cipher=blowfish128,aes128 default-profile=\
default enabled=no keepalive-timeout=60 mac-address=FE:33:DE:01:70:FB \
max-mtu=1500 mode=ip netmask=24 port=1194 require-client-certificate=no
/interface pptp-server server
set authentication=mschap1,mschap2 default-profile=default-encryption \
enabled=no keepalive-timeout=30 max-mru=1460 max-mtu=1460 mrru=disabled
/interface sstp-server server
set authentication=pap,chap,mschap1,mschap2 certificate=none default-profile=\
default enabled=no keepalive-timeout=60 max-mru=1500 max-mtu=1500 mrru=\
disabled port=443 verify-client-certificate=no
/interface wireless align
set active-mode=yes audio-max=-20 audio-min=-100 audio-monitor=\
00:00:00:00:00:00 filter-mac=00:00:00:00:00:00 frame-size=300 \
frames-per-second=25 receive-all=no ssid-all=no
/interface wireless sniffer
set channel-time=200ms file-limit=10 file-name="" memory-limit=10 \
multiple-channels=no only-headers=no receive-errors=no streaming-enabled=\
no streaming-max-rate=0 streaming-server=0.0.0.0
/interface wireless snooper
set channel-time=200ms multiple-channels=yes receive-errors=no
/ip accounting
set account-local-traffic=no enabled=no threshold=256
/ip accounting web-access
set accessible-via-web=no address=0.0.0.0/0
/ip address
add address=192.168.11.1/24 disabled=no interface=Local network=192.168.11.0
add address=192.168.12.1/24 disabled=no interface=Antena network=192.168.12.0
add address=192.168.10.4/24 disabled=no interface=Public network=192.168.10.0
/ip dhcp-server config
set store-leases-disk=5m
/ip dhcp-server network
add address=192.168.12.0/24 comment="hotspot network" dhcp-option="" \
dns-server="" gateway=192.168.12.1 ntp-server="" wins-server=""
/ip dns
set allow-remote-requests=yes cache-max-ttl=1w cache-size=2048KiB \
max-udp-packet-size=4096 servers=203.130.193.74,203.130.206.250
/ip firewall connection tracking
set enabled=yes generic-timeout=10m icmp-timeout=10s tcp-close-timeout=10s \
tcp-close-wait-timeout=10s tcp-established-timeout=1d \
tcp-fin-wait-timeout=10s tcp-last-ack-timeout=10s \
tcp-syn-received-timeout=5s tcp-syn-sent-timeout=5s tcp-syncookie=no \
tcp-time-wait-timeout=10s udp-stream-timeout=3m udp-timeout=10s
/ip firewall filter
add action=passthrough chain=unused-hs-chain comment=\
"place hotspot rules here" disabled=yes
/ip firewall nat
add action=passthrough chain=unused-hs-chain comment=\
"place hotspot rules here" disabled=yes to-addresses=0.0.0.0
add action=masquerade chain=srcnat disabled=no out-interface=Public
add action=masquerade chain=srcnat comment="masquerade hotspot network" \
disabled=no src-address=192.168.12.0/24 to-addresses=0.0.0.0
add action=dst-nat chain=dstnat disabled=no dst-address=192.168.10.4 \
dst-port=3389 in-interface=Public protocol=tcp to-addresses=192.168.11.2 \
to-ports=3389
/ip firewall service-port
set ftp disabled=no ports=21
set tftp disabled=no ports=69
set irc disabled=no ports=6667
set h323 disabled=no
set sip disabled=no ports=5060,5061 sip-direct-media=yes
set pptp disabled=no
/ip hotspot service-port
set ftp disabled=no ports=21
/ip hotspot user
add disabled=no name=admin password=78121 profile=default
add disabled=yes name=siswa password=siswa profile=siswa
/ip hotspot walled-garden
add action=allow disabled=no dst-host=s26.postimg.org dst-port=80
/ip neighbor discovery
set Public disabled=no
set Local disabled=no
set Antena disabled=no
/ip proxy
set always-from-cache=no cache-administrator=webmaster cache-hit-dscp=4 \
cache-on-disk=no enabled=no max-cache-size=unlimited \
max-client-connections=600 max-fresh-time=3d max-server-connections=600 \
parent-proxy=0.0.0.0 parent-proxy-port=0 port=8080 serialize-connections=\
no src-address=0.0.0.0
/ip route
add disabled=no distance=1 dst-address=0.0.0.0/0 gateway=192.168.10.1 scope=\
30 target-scope=10
/ip service
set telnet address="" disabled=no port=23
set ftp address="" disabled=no port=21
set www address="" disabled=no port=8081
set ssh address="" disabled=no port=222
set www-ssl address="" certificate=none disabled=yes port=443
set api address="" disabled=yes port=8728
set winbox address="" disabled=no port=8291
/ip smb
set allow-guests=yes comment=MikrotikSMB domain=MSHOME enabled=no interfaces=\
all
/ip smb shares
set [ find default=yes ] comment="default share" directory=/pub disabled=no \
max-sessions=10 name=pub
/ip smb users
set [ find default=yes ] disabled=no name=guest password="" read-only=yes
/ip socks
set connection-idle-timeout=2m enabled=no max-connections=200 port=1080
/ip traffic-flow
set active-flow-timeout=30m cache-entries=4k enabled=no \
inactive-flow-timeout=15s interfaces=all
/ip upnp
set allow-disable-external-interface=yes enabled=no show-dummy-rule=yes
/ipv6 nd
set [ find default=yes ] advertise-dns=no advertise-mac-address=yes disabled=\
no hop-limit=unspecified interface=all managed-address-configuration=no \
mtu=unspecified other-configuration=no ra-delay=3s ra-interval=3m20s-10m \
ra-lifetime=30m reachable-time=unspecified retransmit-interval=\
unspecified
/ipv6 nd prefix default
set autonomous=yes preferred-lifetime=1w valid-lifetime=4w2d
/mpls
set dynamic-label-range=16-1048575 propagate-ttl=yes
/mpls interface
set [ find default=yes ] disabled=no interface=all mpls-mtu=1508
/mpls ldp
set distribute-for-default-route=no enabled=no hop-limit=255 loop-detect=no \
lsr-id=0.0.0.0 path-vector-limit=255 transport-address=0.0.0.0 \
use-explicit-null=no
/port firmware
set directory=firmware ignore-directip-modem=no
/ppp aaa
set accounting=yes interim-update=0s use-radius=no
/queue interface
set Public queue=ethernet-default
set Local queue=ethernet-default
set Antena queue=ethernet-default
/radius
add accounting-backup=no accounting-port=1813 address=127.0.0.1 \
authentication-port=1812 called-id="" disabled=no domain="" realm="" \
secret=22222222 service=hotspot timeout=300ms
/radius incoming
set accept=yes port=3799
/routing bfd interface
set [ find default=yes ] disabled=no interface=all interval=0.2s min-rx=0.2s \
multiplier=5
/routing igmp-proxy
set query-interval=2m5s query-response-interval=10s quick-leave=no
/routing mme
set bidirectional-timeout=2 gateway-class=none gateway-keepalive=1m \
gateway-selection=no-gateway origination-interval=5s preferred-gateway=\
0.0.0.0 timeout=1m ttl=50
/routing pim
set switch-to-spt=yes switch-to-spt-bytes=0 switch-to-spt-interval=1m40s
/routing rip
set distribute-default=never garbage-timer=2m metric-bgp=1 metric-connected=1 \
metric-default=1 metric-ospf=1 metric-static=1 redistribute-bgp=no \
redistribute-connected=no redistribute-ospf=no redistribute-static=no \
routing-table=main timeout-timer=3m update-timer=30s
/routing ripng
set distribute-default=never garbage-timer=2m metric-bgp=1 metric-connected=1 \
metric-default=1 metric-ospf=1 metric-static=1 redistribute-bgp=no \
redistribute-connected=no redistribute-ospf=no redistribute-static=no \
timeout-timer=3m update-timer=30s
/snmp
set contact="" enabled=no engine-id="" location="" trap-generators="" \
trap-target="" trap-version=1
/system clock
set time-zone-name=Asia/Jakarta
/system clock manual
set dst-delta=+00:00 dst-end="jan/01/1970 00:00:00" dst-start=\
"jan/01/1970 00:00:00" time-zone=+00:00
/system console
set [ find port=serial0 ] channel=0 disabled=no port=serial0 term=vt102
set [ find vcno=1 ] channel=0 disabled=no term=linux
set [ find vcno=2 ] channel=0 disabled=no term=linux
set [ find vcno=3 ] channel=0 disabled=no term=linux
set [ find vcno=4 ] channel=0 disabled=no term=linux
set [ find vcno=5 ] channel=0 disabled=no term=linux
set [ find vcno=6 ] channel=0 disabled=no term=linux
set [ find vcno=7 ] channel=0 disabled=no term=linux
set [ find vcno=8 ] channel=0 disabled=no term=linux
/system console screen
set blank-interval=10min line-count=25
/system gps
set channel=0 enabled=no set-system-time=no
/system hardware
set multi-cpu=yes
/system health
set state-after-reboot=enabled
/system identity
set name=MikroTik
/system lcd
set contrast=0 enabled=no port=parallel type=24x4
/system lcd page
set time disabled=yes display-time=5s
set resources disabled=yes display-time=5s
set uptime disabled=yes display-time=5s
set packets disabled=yes display-time=5s
set bits disabled=yes display-time=5s
set version disabled=yes display-time=5s
set identity disabled=yes display-time=5s
set Antena disabled=yes display-time=5s
set Local disabled=yes display-time=5s
set Public disabled=yes display-time=5s
/system logging
set 0 action=memory disabled=no prefix="" topics=info
set 1 action=memory disabled=no prefix="" topics=error
set 2 action=memory disabled=no prefix="" topics=warning
set 3 action=echo disabled=no prefix="" topics=critical
/system note
set note="" show-at-login=yes
/system ntp client
set enabled=yes mode=unicast primary-ntp=180.211.88.5 secondary-ntp=\
113.52.148.37
/system ntp server
set broadcast=no broadcast-addresses="" enabled=no manycast=yes multicast=no
/system resource irq
set 0 cpu=auto
set 1 cpu=auto
set 2 cpu=auto
set 3 cpu=auto
set 4 cpu=auto
set 5 cpu=auto
set 6 cpu=auto
set 7 cpu=auto
set 8 cpu=auto
/system resource irq rps
set Public disabled=no
set Local disabled=no
set Antena disabled=no
/system scheduler
add disabled=no interval=1d name=siswa_on on-event=":foreach u in=[/ip hotspot\
\_user find] do={:if ([/ip hotspot user get \$u profile]=\"siswa\") do={:l\
og warning \"siswa : \$[/ip hotspot user get \$u name] enable\"\r\
\n/ip hotspot user enable \$u}}}" policy=\
ftp,reboot,read,write,policy,test,winbox,password,sniff,sensitive,api \
start-date=apr/25/2014 start-time=07:00:00
add disabled=no interval=1d name=siswa_off on-event=":foreach u in=[/ip hotspo\
t user find] do={:if ([/ip hotspot user get \$u profile]=\"siswa\") do={:l\
og warning \"siswa : \$[/ip hotspot user get \$u name] disable\"\r\
\n/ip hotspot user disable \$u}}}" policy=\
ftp,reboot,read,write,policy,test,winbox,password,sniff,sensitive,api \
start-date=apr/25/2014 start-time=16:00:00
/system upgrade mirror
set check-interval=1d enabled=no primary-server=0.0.0.0 secondary-server=\
0.0.0.0 user=""
/system watchdog
set auto-send-supout=no automatic-supout=yes no-ping-delay=5m watch-address=\
none watchdog-timer=yes
/tool bandwidth-server
set allocate-udp-ports-from=2000 authenticate=yes enabled=yes max-sessions=\
100
/tool e-mail
set address=0.0.0.0 from=<> password="" port=25 starttls=no user=""
/tool graphing
set page-refresh=300 store-every=5min
/tool mac-server
set [ find default=yes ] disabled=no interface=all
/tool mac-server mac-winbox
set [ find default=yes ] disabled=no interface=all
/tool mac-server ping
set enabled=yes
/tool netwatch
add comment=internet-down-hotspot disabled=no down-script=":local dumplist [/i\
p hotspot active find]\r\
\n:foreach i in=\$dumplist do={\r\
\n /ip hotspot active remove \$i\r\
\n}\r\
\n:local dumplist [/ip hotspot cookie find]\r\
\n:foreach i in=\$dumplist do={\r\
\n /ip hotspot cookie remove \$i\r\
\n}" host=8.8.8.8 interval=30s timeout=1s up-script=""
/tool sms
set allowed-number="" channel=0 keep-max-sms=0 receive-enabled=no secret=""
/tool sniffer
set file-limit=1000KiB file-name="" filter-ip-address="" filter-ip-protocol=\
"" filter-mac-address="" filter-mac-protocol="" filter-port="" \
filter-stream=yes interface=all memory-limit=100KiB memory-scroll=yes \
only-headers=no streaming-enabled=no streaming-server=0.0.0.0
/tool traffic-generator
set latency-distribution-scale=10 test-id=0
/tool user-manager router
add coa-port=3799 customer=admin disabled=no ip-address=127.0.0.1 log=\
auth-fail name=hotspot shared-secret=2222222222 use-coa=no
/user aaa
set accounting=yes default-group=read exclude-groups="" interim-update=0s \
use-radius=no
REMOTE MIKROTIK MELALUI PFSENSE

Kita dapat mengakses semua perangkat komputer (windows rdp, linux diskless) dan server windows maupun server linux melalui mikrotik (ssh, ftp, user manager, winbox) yang diletakkan setelah PFsense Router. langkah-langkah :
1. membuat NAT di Modem
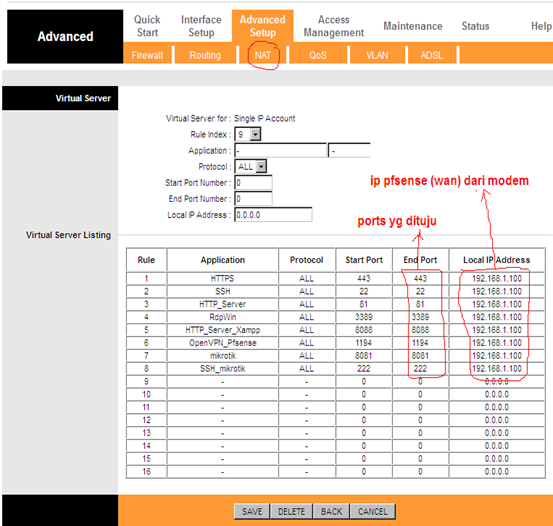
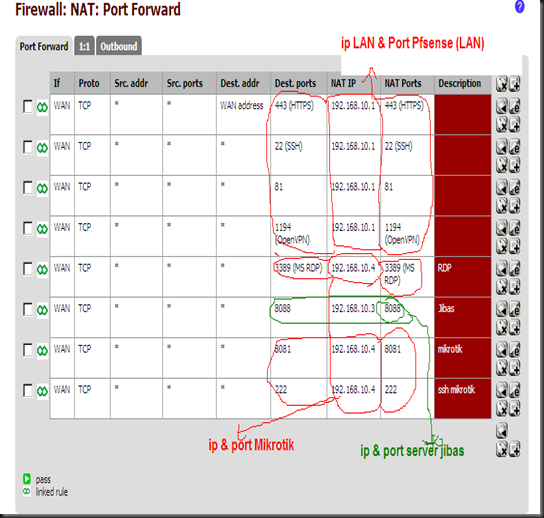
2. membuat NAT di Pfsense ( Firewall – NAT )

Hasilnya :
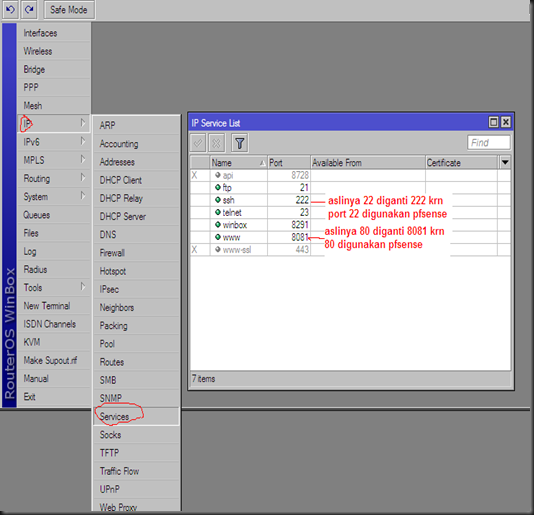
3. rubah port mikrotik yg diperlukan ( ip – services )
4. membuat nat di mikrotik (ip – firewall – NAT)
masukkan script dibawah ini melalui terminal dan jgn lupa sesuaikan ip publik (192.168.10.4) dan ip komputer (192.168.11.2) tujuan anda
/ip firewall nat
add action=dst-nat chain=dstnat disabled=no dst-address=192.168.10.4 \
dst-port=3389 in-interface=Public protocol=tcp to-addresses=192.168.11.2 \
to-ports=3389

5. sekarang saatnya mencoba dari internet dengan menggunakan ip publik speedy. untuk mengetahui ip publik speedy

6. buka browser dan ketikkan http://ippublic:port contoh http://36.76.178.238:3389
Semoga bermanfaat
Sabtu, 26 April 2014
Pemeberitahuan Koneksi Internet via Loginpage Mikrotik
Agar User Hotspot Mikrotik tahu apakah internet anda sedang online atau offline dibawah ini panduan sederhananya.
1. edit file login.html dan letakkkan coding dibawah ini dimana saja dan jangan lupa disave
<center><img src='http://s26.postimg.org/ce70rb3a1/internet_up_hostpot.jpg'
onerror="this.src='img/internet_down_hostpot.jpg'"/align="middle"></center>
2.buka new termina dan masukkan script dibawah ini
/ip hotspot walled-garden
add action=allow disabled=no dst-host=s26.postimg.org dst-port=80
3.masih di new terminal tambahkan juga script dibawah ini
/tool netwatch
add comment=internet-down-hotspot disabled=no down-script=":local dumplist [/ip hotspot active find]\r\
\n:foreach i in=\$dumplist do={\r\
\n /ip hotspot active remove \$i\r\
\n}\r\
\n:local dumplist [/ip hotspot cookie find]\r\
\n:foreach i in=\$dumplist do={\r\
\n /ip hotspot cookie remove \$i\r\
\n}" host=8.8.8.8 interval=30s timeout=1s up-script=""
4.Masukkan file internet_down_hostpot.jpg pada folder hotspot/img mikrotik anda
5. Selamat Mencoba. Dan Terima kasih
1. edit file login.html dan letakkkan coding dibawah ini dimana saja dan jangan lupa disave
<center><img src='http://s26.postimg.org/ce70rb3a1/internet_up_hostpot.jpg'
onerror="this.src='img/internet_down_hostpot.jpg'"/align="middle"></center>
2.buka new termina dan masukkan script dibawah ini
/ip hotspot walled-garden
add action=allow disabled=no dst-host=s26.postimg.org dst-port=80
3.masih di new terminal tambahkan juga script dibawah ini
/tool netwatch
add comment=internet-down-hotspot disabled=no down-script=":local dumplist [/ip hotspot active find]\r\
\n:foreach i in=\$dumplist do={\r\
\n /ip hotspot active remove \$i\r\
\n}\r\
\n:local dumplist [/ip hotspot cookie find]\r\
\n:foreach i in=\$dumplist do={\r\
\n /ip hotspot cookie remove \$i\r\
\n}" host=8.8.8.8 interval=30s timeout=1s up-script=""
4.Masukkan file internet_down_hostpot.jpg pada folder hotspot/img mikrotik anda
5. Selamat Mencoba. Dan Terima kasih
Jumat, 25 April 2014
NTP Client di Mikrotik
Agar Mikrotik kita selalu uptodate waktunya dengan jam dunia maka kita harus memberikan input script
/system ntp client
set enabled=yes mode=unicast primary-ntp=180.211.88.5 secondary-ntp=113.52.148.37
/system ntp client
set enabled=yes mode=unicast primary-ntp=180.211.88.5 secondary-ntp=113.52.148.37
Scheduler Profile Hotspot di Mikrotik
Untuk membatasi waktu Login dan Logout Hotspot Mikrotik berdasarkan Profile, harap diganti atau disesuaikan Profilenya
Contoh : profile "siswa"
script enable
:foreach u in=[/ip hotspot user find] do={:if ([/ip hotspot user get $u profile]="siswa") do={:log warning "siswa : $[/ip hotspot user get $u name] enable"
/ip hotspot user enable $u}}}
script disable
:foreach u in=[/ip hotspot user find] do={:if ([/ip hotspot user get $u profile]="siswa") do={:log warning "siswa : $[/ip hotspot user get $u name] disable"
/ip hotspot user disable $u}}}
script diatas kita masukkan kedalam
/system scheduler pada mikrotik kita dan atur waktunya
/system scheduler
add disabled=no interval=1d name=siswa_on on-event=":foreach u in=[/ip hotspot\
\_user find] do={:if ([/ip hotspot user get \$u profile]=\"siswa\") do={:l\
og warning \"siswa : \$[/ip hotspot user get \$u name] enable\"\r\
\n/ip hotspot user enable \$u}}}" policy=\
ftp,reboot,read,write,policy,test,winbox,password,sniff,sensitive,api \
start-date=apr/25/2014 start-time=07:00:00
add disabled=no interval=1d name=siswa_off on-event=":foreach u in=[/ip hotspo\
t user find] do={:if ([/ip hotspot user get \$u profile]=\"siswa\") do={:l\
og warning \"siswa : \$[/ip hotspot user get \$u name] disable\"\r\
\n/ip hotspot user disable \$u}}}" policy=\
ftp,reboot,read,write,policy,test,winbox,password,sniff,sensitive,api \
start-date=apr/25/2014 start-time=16:00:00
Semoga bermanfaat.
Contoh : profile "siswa"
script enable
:foreach u in=[/ip hotspot user find] do={:if ([/ip hotspot user get $u profile]="siswa") do={:log warning "siswa : $[/ip hotspot user get $u name] enable"
/ip hotspot user enable $u}}}
script disable
:foreach u in=[/ip hotspot user find] do={:if ([/ip hotspot user get $u profile]="siswa") do={:log warning "siswa : $[/ip hotspot user get $u name] disable"
/ip hotspot user disable $u}}}
script diatas kita masukkan kedalam
/system scheduler pada mikrotik kita dan atur waktunya
/system scheduler
add disabled=no interval=1d name=siswa_on on-event=":foreach u in=[/ip hotspot\
\_user find] do={:if ([/ip hotspot user get \$u profile]=\"siswa\") do={:l\
og warning \"siswa : \$[/ip hotspot user get \$u name] enable\"\r\
\n/ip hotspot user enable \$u}}}" policy=\
ftp,reboot,read,write,policy,test,winbox,password,sniff,sensitive,api \
start-date=apr/25/2014 start-time=07:00:00
add disabled=no interval=1d name=siswa_off on-event=":foreach u in=[/ip hotspo\
t user find] do={:if ([/ip hotspot user get \$u profile]=\"siswa\") do={:l\
og warning \"siswa : \$[/ip hotspot user get \$u name] disable\"\r\
\n/ip hotspot user disable \$u}}}" policy=\
ftp,reboot,read,write,policy,test,winbox,password,sniff,sensitive,api \
start-date=apr/25/2014 start-time=16:00:00
Semoga bermanfaat.
Senin, 06 Agustus 2012
MIKROTIK RB750 DENGAN PFSENSE + LUSCA PROXY
modem
|
switch
|----(port1) ---------| |-----------to pfsense wan
MIKROTIK RB750 |
|----(port3) --Kabel UTP CROSS------|
|----(port2) --to switch to clients
======================
pfsense wan : DHCP dari Modem
pfsense lan : 192.168.12.1/24 port proxy 3128 LUSCA
proxy : 192.168.12.15/24
lan : 192.168.10.15/24
modem : 192.168.3.1/24 (DHCP)
ip clients : 192.168.10.xxx dst
======================
setting interface
Code:
/interface set 0 name=public
/interface set 1 name=lan
/interface set 2 name=proxy
======================
setting ip address
code:
/ip address
add address=192.168.3.2/24 network=192.168.3.0 broadcast=192.168.3.255 interface=public comment="" disabled=no
add address=192.168.10.15/24 network=192.168.10.0 broadcast=192.168.10.255 interface=lan comment="" disabled=no
add address=192.168.12.15/24 network=192.168.12.0 broadcast=192.168.12.255 interface=proxy comment="" disabled=no
=======================
setting route:
Code:
/ip route add dst-address=0.0.0.0/0 gateway=192.168.3.1 scope=255 target-scope=10 comment="" disabled=no
=======================
setting dns:
Code:
/ip dns set allow-remote-requests=yes cache-max-ttl=1w cache-size=5000KiB max-udp-packet-size=512 servers=10.17.3.245,10.17.3.252 (dns fren)
/ip dns static add name="192.168.3.1" address=192.168.3.1 ttl=1d
========================
setting nat:
Code:
/ip firewall nat
add chain=srcnat action=masquerade out-interface=public
add chain=dstnat action=redirect to-ports=3128 protocol=tcp src-address=192.168.10.0/24 in-interface=lan dst-port=80 (Bila menggunakan web proxy internal)
add chain=dstnat action=dst-nat to-addresses=192.168.12.1 to-ports=3128 protocol=tcp src-address=192.168.10.0/24 in-interface=lan dst-port=80 (proxy external)
add chain=srcnat action=masquerade out-interface=proxy (agar bisa buka pfsense/putty/winscp diclient)
/ip firewall nat print
0 chain=srcnat action=masquerade out-interface=public
1 X chain=dstnat action=redirect to-ports=3128 protocol=tcp src-address=192.168.10.0/24 in-interface=lan
dst-port=80
2 chain=dstnat action=dst-nat to-addresses=192.168.12.1 to-ports=3128 protocol=tcp
src-address=192.168.10.0/24 in-interface=lan dst-port=80
3 chain=srcnat action=masquerade out-interface=proxy
========================
setting manggle:
Code:
/ip firewall mangle
add chain=forward content="X-Cache: HIT" action=mark-connection new-connection-mark=squid_con passthrough=yes comment="" disabled=no
add chain=forward connection-mark=squid_con action=mark-packet new-packet-mark=squid_pkt passthrough=no comment="" disabled=no
add chain=forward connection-mark=!squid_con action=mark-connection new-connection-mark=all_con passthrough=yes comment="" disabled=no
add chain=forward protocol=tcp src-port=80 connection-mark=all_con action=mark-packet new-packet-mark=http_pkt passthrough=no comment="" disabled=no
add chain=forward protocol=icmp connection-mark=all_con action=mark-packet new-packet-mark=icmp_pkt passthrough=no comment="" disabled=no
add chain=forward protocol=tcp dst-port=1973 connection-mark=all_con action=mark-packet new-packet-mark=top_pkt passthrough=no comment="" disabled=no
add chain=forward connection-mark=all_con action=mark-packet new-packet-mark=test_pkt passthrough=no comment="" disabled=no
/ip firewall mangle print
0 chain=forward action=mark-connection new-connection-mark=squid_con passthrough=yes content=X-Cache: HIT
1 chain=forward action=mark-packet new-packet-mark=squid_pkt passthrough=no connection-mark=squid_con
2 chain=forward action=mark-connection new-connection-mark=all_con passthrough=yes
connection-mark=!squid_con
3 chain=forward action=mark-packet new-packet-mark=http_pkt passthrough=no protocol=tcp src-port=80
connection-mark=all_con
4 chain=forward action=mark-packet new-packet-mark=icmp_pkt passthrough=no protocol=icmp
connection-mark=all_con
5 chain=forward action=mark-packet new-packet-mark=top_pkt passthrough=no protocol=tcp dst-port=1973
connection-mark=all_con
6 chain=forward action=mark-packet new-packet-mark=test_pkt passthrough=no connection-mark=all_con
=======================
setting queue :
/queue simple
add name="Squid_HIT" dst-address=0.0.0.0/0 interface=all parent=none packet-marks=squid_pkt direction=both priority=8 queue=default-small/default-small limit-at=0/0 max-limit=0/0 total-queue=default-small disabled=no
add name="Main_Link" dst-address=0.0.0.0/0 interface=all parent=none direction=both priority=8 queue=default-small/default-small limit-at=0/0 max-limit=35000/256000 total-queue=default-small disabled=no
add name="game_tales_of_pirate" dst-address=0.0.0.0/0 interface=all parent=none packet-marks=top_pkt direction=both priority=1 queue=default-small/default-small limit-at=0/0 max-limit=0/0 total-queue=default-small disabled=no
add name="Ping_queue" dst-address=0.0.0.0/0 interface=all parent=none packet-marks=icmp_pkt direction=both priority=2 queue=default-small/default-small limit-at=0/0 max-limit=0/0 total-queue=default-small disabled=no
add name="The_other_port_queue" target-addresses=192.168.12.0/24 dst-address=0.0.0.0/0 interface=all parent=Main_Link packet-marks=http_pkt direction=both priority=8 queue=default-small/default-small limit-at=5000/5000 max-limit=50000/256000 total-queue=default-small disabled=no
add name="another_port" target-addresses=192.168.10.0/24 dst-address=0.0.0.0/0 interface=all parent=Main_Link packet-marks=test_pkt direction=both priority=8 queue=default-small/default-small limit-at=0/0 max-limit=0/256000 total-queue=default-small disabled=no
/queue simple print
0 name="Squid_HIT" dst-address=0.0.0.0/0 interface=all parent=none
packet-marks=squid_pkt direction=both priority=8
queue=default-small/default-small limit-at=0/0 max-limit=0/0
burst-limit=0/0 burst-threshold=0/0 burst-time=0s/0s
total-queue=default-small
1 name="Main_Link" dst-address=0.0.0.0/0 interface=all parent=none
direction=both priority=8 queue=default-small/default-small
limit-at=0/0 max-limit=35k/256k burst-limit=0/0 burst-threshold=0/0
burst-time=0s/0s total-queue=default-small
2 name="game_tales_of_pirate" dst-address=0.0.0.0/0 interface=all
parent=none packet-marks=top_pkt direction=both priority=1
queue=default-small/default-small limit-at=0/0 max-limit=0/0
burst-limit=0/0 burst-threshold=0/0 burst-time=0s/0s
total-queue=default-small
3 name="Ping_queue" dst-address=0.0.0.0/0 interface=all parent=none
packet-marks=icmp_pkt direction=both priority=2
queue=default-small/default-small limit-at=0/0 max-limit=0/0
burst-limit=0/0 burst-threshold=0/0 burst-time=0s/0s
total-queue=default-small
Minggu, 27 Mei 2012
Membangun Warnet Speedy dengan Mikrotik RB750

01 | xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx |
02 | Jasa Setting Online Mikrotik dan Lusca Proxy |
11 | IP Modem : 192.168.1.1 |
12 |
13 | Setting Mikrotik |
14 | ============= |
15 |
16 | Menghapus Konfigurasi Default Mikrotik |
17 | ================================ |
18 |
19 | 1. Login melalui Winbox |
20 | 2. Pilih menu New Terminal |
21 | 3. Ketik perintah dibawah ini : |
22 | /system reset |
23 | y |
24 |
25 | maka router akan disconnect |
26 | 4. Login kembali menggunakan Winbox |
27 | 5. Klik tombol Remove Configuration |
28 |
29 |
30 | Setting Router Gateway |
31 | =================== |
32 |
33 | Petunjuk |
34 | ------------ |
35 | 1. Login melalui Winbox |
36 | 2. Pilih menu New Terminal |
37 | 3. Copy Paste skrip dibawah ini : |
38 |
39 | Set interface ethernet |
40 | ------------------------------- |
41 |
42 | /interface ethernet |
43 | set 0 name=ether1-public |
44 | set 1 name=ether2-local |
45 | set 2 name=ether3 |
46 | set 3 name=ether4 |
47 | set 4 name=ether5 |
48 |
49 | Set interface IP Address |
50 | ---------------------------------- |
51 |
52 | /ip address |
53 | add address=192.168.1.2/24 disabled=no interface=ether1-public |
54 | add address=192.168.2.1/24 disabled=no interface=ether2-local |
55 |
56 |
57 | Set Route |
58 | -------------- |
59 |
60 | /ip route |
61 | add disabled=no distance=1 dst-address=0.0.0.0/0 gateway=192.168.1.1 scope=30 target-scope=10 |
62 |
63 | Set NAT Masquerade |
64 | ------------------------------ |
65 |
66 | /ip firewall nat |
67 | add action=masquerade chain=srcnat disabled=no out-interface=ether1-public |
68 |
69 | Set DNS |
70 | ------------ |
71 |
72 | /ip dns |
73 | set allow-remote-requests=yes cache-max-ttl=1w cache-size=2048KiB max-udp-packet-size=51 |
74 | 202.134.1.10 |
75 |
76 |
77 | Setting Komputer Klien Warnet |
78 | ======================== |
79 |
80 | IP Config : |
81 | ---------------- |
82 |
83 | IP Address : 192.168.2.2 |
84 | Subnet Mask : 255.255.255.0 |
85 | Gateway : 192.168.2.1 |
86 | Preferred DNS Server : 192.168.2.1 |
Cara Remote Mikrotik Winbox melalui internet jarak jauh dengan ISP Speedy IP Dinamis dan ChangeIP.net
Rate This
Ok brother and sister because to many questions about How to Remote Mikrotik via Internet while your only got Dynamic Public IP Address from the ISP, gitu ya bahasa inggrisnya?, kira2 artinya bagaimana cara remote mikrotik melalui internet sementara kita hanya dapat IP Publik yang dinamis dari ISP misalnya Speedy. Tutorial ini saya buat dari pertanyaan Mas Paijo (bukan nama sebenarnya) .hihihi . pertanyaan tentang cara remote Mikrotik via internet sementara dia menggunakan IP Publik dinamis http://farounet.wordpress.com/2011/05/07/remote-mikrotik-winbox-melalui-internet-jarak-jauh-dengan-isp-speedy-ip-dinamis-dan-dyndns/
Berikut adalah isi pertanyaan Mas Paijo
#1
wah gan bayar kalo mau add host di dyndns bos , masak gratis ??? ane udh coba ga bisa ini hrs meski trial pun dia minta CC(credit card valid) number
#2
mas ini memeng gratis acounta tapi dia minta Provide payment information nah ini gw aja kaga punya mas yg nama CC or credit card dll… apa yg harus saya lakuin ini macet dah gak bisa nyoba tutorial mas diatas. thanks sebelumnya
Ya emang sekarang Dyndns lebih ketat dalam proses registrasi (butuh CC). CC tau kan? Credit Card atau kartu ngutang …hehe, padahal dulu simple sekali dan bisa dapat 2 hostname sekarang ? ya paling cuma dapat 1 hostname Free itu pun dengan proses registrasi seperti kata Mas Paijo tadi.
Ya udah, daripada pusing mikirin daftar di Dyndns yang katanya gak gratis lagi mending cari web lain yang masih menyediakan layanan dynamic DNS gratis FREE seperti Changeip.net
Tunjuk poin aja deh, berikut dibawah ini ritualnya :
Bismillahirrahmanirrahim
- Daftar di www.changeip.net
- Tambahkan hostname
-
Buka winbox, tambahkan skrip dibawah ini. Menu System > Script

01 | :local user "USERKAMU" |
02 | :local pass "PASSWORDUSERKAMU" |
03 | :local host "HOSTNAMEKAMU" |
04 |
05 | ############## |
06 | ############## |
07 | :global lastwanip; |
08 | :if ([ :typeof $lastwanip ] = "nothing" ) do={ :global lastwanip 0.0.0.0 }; |
09 | :local wanip [:resolve $host]; |
10 | :if ( $wanip != $lastwanip ) do={ |
11 | /tool fetch mode=http address="checkip.dyndns.org" src-path="/" dst-path="/dyndns.checkip.html" |
12 | :local result [/file get dyndns.checkip.html contents] |
13 | :local resultLen [:len $result] |
14 | :local startLoc [:find $result ": " -1] |
15 | :set startLoc ($startLoc + 2) |
16 | :local endLoc [:find $result "</body>" -1] |
17 | :local currentIP [:pick $result $startLoc $endLoc] |
18 | :set lastwanip $currentIP; |
19 | :put [/tool dns-update name=$host address=$currentIP key-name=$user key=$pass ] |
20 |
21 | } |
-
Tambahkan schedule seperti dibawah ini . Menu System > Scheduler




Jangan lupa cendolnya gan dan LIKE nya.. yang mau DONASI jg boleh..hehe
Yang butuh Jasa Setting atau Training kita kontak disini ya :
CALL / SMS : 085840831797 / 08112619565
Y!M : siganteng_k@ymail.com
Email : muhammad.fadilah@gmail.com
BB PIN : 22BBF6DD
Peringatan ! :
- Habis setting bayar ya, jangan melarikan diri. Itu namanya ga tau diri, repot urusan lu dengan yang Maha Pencipta.
- Untuk yang bukan Pelanggan dan Siswa kita, dimohon kalo nanya via YM jangan maksa ya. Kalo mau Tanya silahkan komentar di web ini, Support hanya untuk Pelanggan/Siswa/Donatur dan konsultasi seputar jasa layanan.
- Untuk komentar yang belum dijawab harap sabar, silahkan cari referensi dari web lain sambil menunggu reply dari saya
- Untuk yang butuh jasa kita atau butuh support silahkan gunakan media layanan support yang sudah ada seperti YM, Email, SMS, Telp, Social Network
Konfigurasi Mikrotik dan Squid Proxy
This entry was posted on March 1, 2011, in Mikrotik, Referensi, Tutorial. Bookmark the permalink. 20 Comments
Rate This
Install Squid di ubuntu 10.4
- masuk ke terminal
- ketik sudo su , isi password ubuntu anda
- ketik sudo apt-get update
- ketik sudo apt-get install squid
- Do you want continue [Y] Y
- apt-get install squid squidclient squid-cgi
- apt-get install ccze
Membuat Directory cache
- mkdir /cache1 && mkdir /cache2 && mkdir /cache3 && mkdir /cache4
- touch /var/log/squid/access.log
- touch /var/log/squid/cache.log
Mengaktifkan directory cache
- chown -R proxy.proxy /cache1
- chown -R proxy.proxy /cache2
- chown -R proxy.proxy /cache3
- chown -R proxy.proxy /cache4
- chown -R proxy.proxy /var/log/squid/access.log
Edit Squid.conf
- gedit /etc/squid/squid.conf
Silahkan download file Squid.conf disini (sesuaikan dengan jaringan,memory,hdd dari PC Proxy anda)
Pengecekan file Squid.conf
- squid -k parse
membuat direktori swap
- squid -z
- squid -DFY
Reboot Squid Proxy
cek squid apakah sudah berfungsi
- ps -ax|grep squid
Terakhir jalankan perintah :
iptables -t nat -A POSTROUTING -j MASQUERADE
Download Tulisan selengkapnya disini
Port Game Online di Mikrotik
Port Game Online di Mikrotik
1. Ayo Dance : tcp 18901-18909
2. SealOnline : tcp 1818
3. PointBlank : tcp 39190, udp 40000-40010
4. Lineage2 : tcp 7777
5. GhostOnline : tcp 19101
6. RF-Elven : tcp 27780
7. Perfect world : tcp 29000
8. Rohan : tcp 22100
9. Zeus RO : tcp 5121
10. Dotta : tcp 6000-6152
11. IdolStreet : tcp 2001
12. CrazyKart : 9601-9602
13. WOW AMPM : tcp 8085
14. DriftCity : tcp 11011-11041
15. GetAmped : tcp 13413
16. Yullgang : tcp 19000
17. RAN Online : tcp 5105
18. CrossFire : tcp 10009, udp 12060-12070
19. WarRock : tcp 5340-5352
20. FastBlack : tcp 6000-6001
21. Rose Online : tcp 29200
22. Return Of Warrior : tcp 10402
23. CrazyKart 2 : tcp 9600
25. Luna Online : tcp 15002
26. Runes Of Magic : tcp 16402-16502
27. FreshRO : tcp 5126
28. Tantra Online : tcp 3010
29. Heroes Of Newearth Incatamers : tcp 11031 udp 11100-11125,11440-11460
30. Atlantica : tcp 4300 , ip 203.89.147.0/24
31. ECO Online : tcp Port 12011 , 12110
32. Cabal Indo : tcp Port 15001, 15002
33. X-SHOT : tcp 7341,7451 , udp 7808,3000034. 3 Kingdoms : UDP 42051-42052
35. AVALON : TCP 9376-9377
36. Free Style : TCP 10001-10011,40000, UDP 40040-40500,1293,1479
37. Grand Chase : TCP 9300,9400,9700, UDP 9401,9600
38. Lost Saga : TCP 14009-14010, UDP: 14009-14010
39. CS Online Indonesia : UDP 27017, TCP : 8001,9015,40300-40404,36567
Mereboot Mikrotik
Mereboot Mikrotik
Sebuah Alasan Harus Reboot Wireless
Scriptnya berikut:
/system script name="reboot" owner="admin" \
policy=ftp,reboot,read,write,policy,test,winbox,password,sniff run-count=0\
source=/system reboot
Schedulenya ini:
/system scheduler add name="reboot6am" start-date="jan/01/2009"\
start-time="06:00:00" interval="30m" on-event="{/system reboot;}"
Mudah mudahan script autoreboot interval 30 menit ini bermanfaat untuk anda suatu saat apapun alasannya :P
Automatic Failover dengan Mikrotik
Automatic Failover dengan Mikrotik
Script ini diambil dari sini, akan tetapi saya rubah sedikit, karena belum jalan di mikrotik saya.
Sebelumnya saya akan terangkan skenario-nya,
ISP 1 ————– | |
| Mikrotik | ========= LAN
ISP 2 ————– | |
Sebuah Mikrotik terhubung dengan 2 ISP (WAN), ISP 1 sebagain main link, sedangkan ISP 2 sebagai backup link. Bila ISP 1 down, maka routing internet akan ke ISP 2, jika ISP 1 up kembali, routing kembali ke semula.
Setelah semua dikonfigurasi secara standar, Berikut adalah step2-nya :
1. Beri nilai 1 untuk distance di routing utama (main link), dan nilai 2 untuk routing backup.
2. Define IP Public luar yang bisa di monitoring, misal saya ambil 172.16.64.13 sebagai ip netwatch saya, kemudian tmbahkan routing ke ip tersebut melalui main link.
Misal :
ISP 1 = ADSL
ISP 2 = Cable/IM2

3. Tambahkan script berikut yang berfungsi script fail over dan ip monitoring :
==============================================================
/system script add name=”failover” source={
:if ([/ip route get [/ip route find comment="utama"] disabled]=”yes”) do={/ip route enable [/ip route find comment="utama"]} else={/ip route disable [/ip route find comment="utama"]}
/system script add name=”back2main” source={
:if ([/ip route get [/ip route find comment="utama"] disabled]=”yes”) do={/ip route enable [/ip route find comment="utama"]}
/tool netwatch add host=172.16.64.13 interval=10s timeout=1s down-script=”failover”
/tool netwatch add host=172.16.64.13 interval=10s timeout=1s up-script=”back2main”
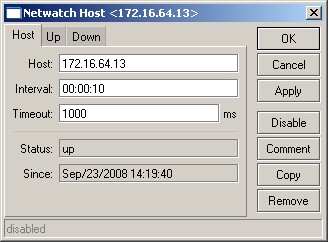
pemberian interval dan timeout silahkan disesuaikan dengan kebutuhan jaringan anda.
keterangan :
Monitoring ke ip 172.16.64.13 setiap 10 detik, bila dideteksi down maka failover script yang berfungsi untuk mendisable routing utama yang aktif, dan sebaliknya, bil ip tersebut up kembali maka mikrotik akan menjalan script back2main untuk meng-enable-kan routing utama.
Silahkan dicoba…..
Tutorial Failover Mikrotik dan External Proxy
Tutorial Failover Mikrotik dan External Proxy
Tutorial Failover Mikrotik dan External Proxy
Pendahuluan
Tutorial ini diperuntukan mesin Mikrotik dengan External Proxy, yang akan dibahas disini adalah bagaimana Mikrotik bisa menonaktifkan perintah redirect port yang dibelokkan ke external proxy ketika mesin server mati atau terputus dengan server atau service port proxy dalam kondisi mati secara tiba-tiba tetapi kondisi mesin masih menyala, dan bagaimana Mikrotik bisa kembali mengaktifkan redirect port ke external proxy ketika terhubung kembali dengan server atau port proxy tersedia kembali. Dengan cara:
1. Mikrotik selalu melakukan ping ke IP server external proxy, jika terputus maka Mikrotik akan menonaktifkan perintah redirect port dan sebaliknya.
2. Disini tidak akan tergantung dengan situs-situs diluar agar kondisinya bisa digaransi, melainkan dari server external proxy akan memantau port proxy-nya sendiri setiap berapa detik sekali, setiap kondisi port proxy mengalami kegagalan maka server akan mengirimkan perintah ke Mikrotik melalui SSH agar Mikrotik menonaktifkan perintah redirect port dan kondisi sebaliknya pula.
Tujuannya adalah ketika tiba-tiba server external proxy dalam kondisi mati sendiri dan daemon proxy down sendiri karena ada sesuatu yang faild maka dari sisi client masih tetapi bisa browsing tanpa memakai external proxy tanpa campur tangan administratornya karena yang bersangkutan sedang tertidur dan keperluan lainnya.
Tutorial ini diperuntukan mesin Mikrotik dengan External Proxy, yang akan dibahas disini adalah bagaimana Mikrotik bisa menonaktifkan perintah redirect port yang dibelokkan ke external proxy ketika mesin server mati atau terputus dengan server atau service port proxy dalam kondisi mati secara tiba-tiba tetapi kondisi mesin masih menyala, dan bagaimana Mikrotik bisa kembali mengaktifkan redirect port ke external proxy ketika terhubung kembali dengan server atau port proxy tersedia kembali. Dengan cara:
1. Mikrotik selalu melakukan ping ke IP server external proxy, jika terputus maka Mikrotik akan menonaktifkan perintah redirect port dan sebaliknya.
2. Disini tidak akan tergantung dengan situs-situs diluar agar kondisinya bisa digaransi, melainkan dari server external proxy akan memantau port proxy-nya sendiri setiap berapa detik sekali, setiap kondisi port proxy mengalami kegagalan maka server akan mengirimkan perintah ke Mikrotik melalui SSH agar Mikrotik menonaktifkan perintah redirect port dan kondisi sebaliknya pula.
Tujuannya adalah ketika tiba-tiba server external proxy dalam kondisi mati sendiri dan daemon proxy down sendiri karena ada sesuatu yang faild maka dari sisi client masih tetapi bisa browsing tanpa memakai external proxy tanpa campur tangan administratornya karena yang bersangkutan sedang tertidur dan keperluan lainnya.
Tutorial ini hanya contoh, silahkan disesuaikan kondisi masing-masing, maka itu sebelumnya saya memberi contoh topology yang saya pakai…
either3
-------------- AP RT/RW NET )))))) ((((((( CLIENT WIFI
|
either0 | either2
MODEM BRIDGE -------------------- MIKROTIK ---------SWITCH ---------- CLIENT WARNET
|
either1 |
| eth0
EXTERNAL PROXY
Keterangan contoh:
IP either1: 192.168.3.254, nama interfaces: to_proxy
IP either2: 192.168.1.254, nama interfaces: to_warnet
IP either3: 192.168.2.245, nama interfaces: to_wifi
IP eth0 external proxy: 192.168.3.253
Disini saya anggap bahwa server proxy sudah diinstall dan berjalan dengan baik, begitu juga kondisi dial modem maupun Mikrotik sudah bisa berjalan tanpa external proxy.
Langkah Pertama
Buat Rule di Mirkotik untuk Redirect port 80/HTTP dan 3128/PROXY dari wifi maupun warnet diarahkan ke external proxy 192.168.3.253 port 3128
-------------- AP RT/RW NET )))))) ((((((( CLIENT WIFI
|
either0 | either2
MODEM BRIDGE -------------------- MIKROTIK ---------SWITCH ---------- CLIENT WARNET
|
either1 |
| eth0
EXTERNAL PROXY
Keterangan contoh:
IP either1: 192.168.3.254, nama interfaces: to_proxy
IP either2: 192.168.1.254, nama interfaces: to_warnet
IP either3: 192.168.2.245, nama interfaces: to_wifi
IP eth0 external proxy: 192.168.3.253
Disini saya anggap bahwa server proxy sudah diinstall dan berjalan dengan baik, begitu juga kondisi dial modem maupun Mikrotik sudah bisa berjalan tanpa external proxy.
Langkah Pertama
Buat Rule di Mirkotik untuk Redirect port 80/HTTP dan 3128/PROXY dari wifi maupun warnet diarahkan ke external proxy 192.168.3.253 port 3128
Code:
/ip firewall mangle
add action=add-src-to-address-list address-list="wifi hot-spot" \
address-list-timeout=1m chain=prerouting \
comment="User online list adding from HotSpot" disabled=no \
in-interface=to_wifi src-address=192.168.2.0/24 \
src-address-type=!local
add action=add-src-to-address-list address-list="warnet" \
address-list-timeout=1m chain=prerouting \
comment="User online list adding from Warnet" disabled=no \
in-interface=to_warnet src-address=192.168.1.0/24 \
src-address-type=!local
/ip firewall nat
add action=dst-nat chain=dstnat comment="Redirect_Proxy_Warnet" \
disabled=no dst-port=80,3128 in-interface=to_warnet \
protocol=tcp src-address-list=warnet \
to-addresses=192.168.3.253 to-ports=3128
add action=dst-nat chain=dstnat comment="Redirect_Proxy_WiFi" \
disabled=no dst-port=80,3128 in-interface=to_wifi \
protocol=tcp src-address-list="wifi hot-spot" \
to-addresses=192.168.3.253 to-ports=3128
Langkah Kedua
Buat script di Mikrotik yang bertujuan selalu mengontrol koneksi dari mikrotik ke external proxy, bila terjadi koneksi terputus akan menonaktifkan redirect dan sebaliknya, dalam interval 1 detik sekali melakukan ping dengan batasan latency maksimal 20ms.
Buat script di Mikrotik yang bertujuan selalu mengontrol koneksi dari mikrotik ke external proxy, bila terjadi koneksi terputus akan menonaktifkan redirect dan sebaliknya, dalam interval 1 detik sekali melakukan ping dengan batasan latency maksimal 20ms.
Code:
/tool netwatch
add comment="" disabled=no down-script="/ip firewall nat set [find comment=\"\
Redirect_Proxy_Warnet\"] disabled=yes\r\
\n/ip firewall nat set [find comment=\"Redirect_Proxy_WiFi\"] disabled=yes\r\
\n:log error \"External Server is DOWN...!\"" host=192.168.3.253 \
interval=1s timeout=20ms up-script="/ip firewall nat set [find comment=\"Redirect_Proxy_Warnet\"] disabled=no\r\
\n/ip firewall nat set [find comment=\"Redirect_Proxy_WiFi\"] disabled=no\r\
\n:log error \"External Server is UP...!\""
Kemudian
diujicoba, cabut kabel UTP yang menuju ke external proxy dan lihat rule
ip firewall nat untuk Redirect port-nya, apakah sudah disabled atau
belum, klo sudah disabled berarti sudah berjalan sesuai harapan.
Dan sebaliknya colokan kembali kabel UTP-nya, seharusnya otomatios akan enable.
Langkah Ketiga
Buat account user di Mikrotik missal dengan nama proxy tanpa password dan beri allow hanya bisa dipakai dari host ber-IP interfaces server external proxy untuk keamanan.
Dan sebaliknya colokan kembali kabel UTP-nya, seharusnya otomatios akan enable.
Langkah Ketiga
Buat account user di Mikrotik missal dengan nama proxy tanpa password dan beri allow hanya bisa dipakai dari host ber-IP interfaces server external proxy untuk keamanan.
Code:
/user
add address=192.168.3.253/32 comment="" disabled=no group=full name=proxy
Langkah Keempat
Buat script di linux (external proxy) tetapi install dahulu repository NMAP karena akan menghandalkan tools tersebut untuk deteksi port proxy.
install NMAP….
Buat script di linux (external proxy) tetapi install dahulu repository NMAP karena akan menghandalkan tools tersebut untuk deteksi port proxy.
install NMAP….
Code:
# apt-get install nmap
buat script di /sbin/failover-proxy…
Code:
pico /sbin/failover-proxy
dan isi script-nya sebagai berikut….
Code:
#!/bin/bash
#######################################################
# DIBUAT OLEH OPiKdesign EMAIL th@opikdesign.com
# DIDEDIKASIKAN UNTUK KOMUNITAS INDONESIA OPENSOURCE
#######################################################
#######################################################
# VARIABLE......
# SILAHKAN DISESUAIKAN
#######################################################
#User Mikrotik tanpa password
user="proxy"
#IP Mikrotik yang terhubung ke proxy
ip_mt="192.168.3.254"
#Comment redirect sesuaikan seperti rule di Mikrotik > ip > firewall > nat
comment_nat_wifi="Redirect_Proxy_WiFi"
comment_nat_warnet="Redirect_Proxy_Warnet"
#Port Proxy
port=3128
#Interval berapa detik sekali
INTERVAL=1
#######################################################
# MULAI BARIS INI......
# JANGAN MERUBAH SCRIPT JIKA TIDAK AHLI
#######################################################
# VARIABLE FILE TEMP
TEMP="/root/failover.status"
# VARIABLE CONNECT SSH KE MIKROTIK
connect_ssh="ssh $user@$ip_mt"
# VARIABLE PERINTAH REDIRECT ENABLE/DISABLE KE MIKROTIK
redirect_dis_wifi='/ip firewall nat set [find comment="'$comment_nat_wifi'"] disabled=yes'
redirect_ena_wifi='/ip firewall nat set [find comment="'$comment_nat_wifi'"] disabled=no'
p firewall nat set [find comment="'$comment_nat_warnet'"] disabled=yes'
redirect_ena_warnet='/ip firewall nat set [find comment="'$comment_nat_warnet'"] disabled=no'
# VARIABLE PENGIRIMAN PESAN LOG KE MIKROTIK
log_down='/log error message="Proxy Server is DOWN...!"'
log_up='/log error message="Proxy Server is UP...!"'
# PENGECEKAN AWAL: PORT PROXY DAN PENGATURAN KE MIKROTIK
nmap localhost | grep $port > /dev/null 2>&1
TEST_SQUID=$?
if [ $TEST_SQUID -ne 0 ]; then
$connect_ssh $redirect_dis_wifi
$connect_ssh $redirect_dis_warnet
$connect_ssh $log_down
echo "disable" > $TEMP
else
$connect_ssh $redirect_ena_wifi
$connect_ssh $redirect_ena_warnet
p
echo "enable" > $TEMP
fi
# PENGECEKAN SECARA CONTINUE: PORT PROXY DAN PENGATURAN KE MIKROTIK
while : ; do
nmap localhost | grep $port > /dev/null 2>&1
TEST_SQUID=$?
if [ $TEST_SQUID -ne 0 ]; then
cat $TEMP | grep enable > /dev/null 2>&1
STATUS=$?
if [ $STATUS -ne 1 ]; then
$connect_ssh $redirect_dis_wifi
$connect_ssh $redirect_dis_warnet
$connect_ssh $log_down
echo "disable" > $TEMP
grep disable > /dev/null 2>&1
STATUS=$?
if [ $STATUS -ne 1 ]; then
$connect_ssh $redirect_ena_wifi
$connect_ssh $redirect_ena_warnet
$connect_ssh $log_up
echo "enable" > $TEMP
fi
fi
sleep $INTERVAL
done
#######################################################
# AKHIR SCRIPT
#######################################################
Code:
# chmod +x /sbin/failover-proxyLangkah Kelima
Agar setiap kali si server external proxy booting/restart selalu dipanggil dan berjalan sebagai daemon maka tambahkan baris perintah dibawah ini di dalam file /etc/rc.local….
Code:
nohup /sbin/failover-proxy &Langkah Keenam (terakhir)
Reboot server external proxy-nya, kemudian uji coba dengan memantau Mikrotik ip firewall nat, coba daemon squid-nya matikan dan seharusnya rule redirect di Mikrotik otomatis disable dan di log pasti ada pesan tanda merah… dan sebaliknya hidupkan kembali daemon squid-nya, seharusnya rule redirect di Mikrotik akan aktif kembali dan ada pesan di log-nya.
untuk mematikan daemon squid/proxy
Code:
# service squid stopuntuk menghidupkan kemabli daemon squid/proxy
Code:
# service squid start-----------------------------
Silahkan tutorial ini dengan bebas dipakai dan dikembangkan namun mohon penghargaannya jika tutorial ini akan ditulis kembali ditempat lain semisal di forum, wiki maupun dimanapun… mohon menyebutkan sumbernya dengan memberikan link thread ini.
------------------------------
sumber:komunitas indonesia open source
Langganan:
Postingan (Atom)



